How Blockchain Powers the Agent Swarm
We are shifting toward the Agentic Web.
For the past two decades, we’ve lived in the “Internet of Information.” You click a link, a server sends data, and you read it. It was a library; you were the researcher.
But that era is ending. We are shifting toward the Agentic Web.
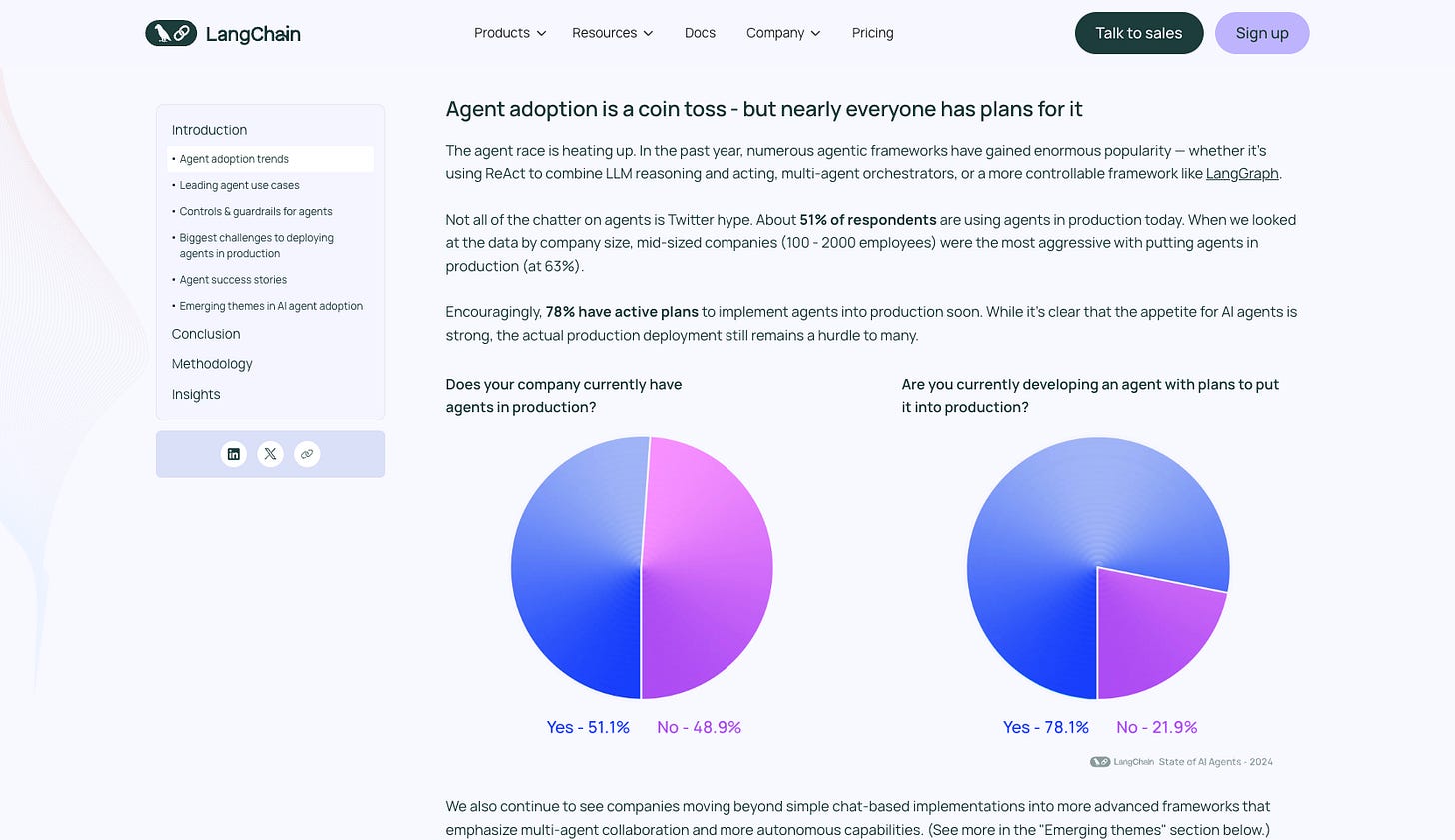
In this new world, the main users of the internet won’t be humans browsing—they will be Autonomous AI Agents. These aren’t just chatbots that talk; they are software entities that perceive, plan, and actually do work. According to LangChain’s 2024 report, companies are already moving past the “hype” phase, deploying agents to handle customer service and internal tooling.
But how do you prevent a swarm of independent, decision-making bots from descending into chaos? The answer requires a new stack of technology that merges the “Brain” of modern AI orchestration with the “Spine” of blockchain infrastructure.
The Agent Builder’s Toolkit: How to Build a Swarm
Before we get to the blockchain layer, we need to understand how developers are actually coding these swarms today. It helps to think of the technology in two layers: the Brain (Orchestration) and the Economy (Infrastructure).
Part 1: The Brain – Orchestrating the Swarm
You can’t just spin up 50 AI bots and hope for the best. You need a manager. Below are some of the most popular options for you to use to build the agent swarm.
OpenAI Swarm (The Sandbox): Released as an experimental framework, this is great for learning the basics. It uses a concept called “Handoffs”—where one agent (e.g., a Triage Agent) explicitly hands a task to another (e.g., a Sales Agent). It is lightweight and stateless, making it perfect for simple, linear chains of command, but OpenAI explicitly warns it is not yet meant for heavy production.
LangGraph (The Factory): If OpenAI Swarm is a whiteboard sketch, LangGraph is the assembly line. It treats agent workflows as a “cyclic graph,” allowing agents to loop, remember past mistakes (state), and retry tasks. It supports complex patterns like “Hierarchical Teams” (a boss agent managing worker agents) or “Network” patterns (peer-to-peer collaboration), making it the go-to for production-grade swarms.
Part 2: The Society – Search, Discovery, and Negotiation
Once you have the “Brain” built in LangGraph, you need to give it an economy to live in. This is where recent blockchain protocols shine.
Blockchain has proved its standing as one of the most secure technologies in the last two decades. I believe when you come to this article, you are already aware of how secure a blockchain is; if not, there are thousands of research papers and articles explaining this. We recommend this article, “Blockchain Security” from IBM, to prepare you with some prior knowledge about blockchain, not too long, not too short. Below are some blockchain technologies that are involved in the innovation of agent swarm:
Infrastructure & Ecosystems
These projects focus on the foundational layers, allowing agents to be built, deployed, and interact effectively.
Virtuals Protocol (The Launchpad): This project positions itself as a full-stack platform and AI-agent launchpad, often called the “Shopify of AI agents.” It uses a specific framework and an Agent Commerce Protocol (ACP) to allow developers—even those without extensive coding skills—to build, own, and monetize multimodal, tokenized AI agents (e.g., trading bots, gaming NPCs) on chains like Base and Solana.
Kite (The Payment Backbone): Described as the “First AI Payment Blockchain,” Kite is a purpose-built Layer 1 blockchain for the agentic economy. It focuses on providing essential services for agents, such as:
Cryptographic Identity: Giving AI models and agents a unique, verifiable identity for traceability and governance.
Programmable Governance: Offering granular control over the permissions and constraints of autonomous agents.
Agentic Payment: Enabling near-zero fee, instant value transfers with native stablecoin access for machine-to-machine transactions.
Fetch.ai / ASI Alliance (The Marketplace): This is the most established network for Autonomous Economic Agents (AEAs). Instead of a single bot working in a silo, Fetch.ai creates a decentralized world where agents can find each other and negotiate. For example, a “Supply Chain Agent” can autonomously search the network for a “Shipping Agent,” negotiate a price in FET tokens, and book a delivery without human help. (Reference: https://fetch.ai/blog/agent-anatomy)
Phala Network (The Safe): One big fear is that a “rogue admin” could peek at an agent’s private data. Phala uses TEEs (Trusted Execution Environments)—special hardware enclaves that ensure the agent’s code runs exactly as programmed and its data is encrypted, even from the server's owner. (Reference: https://phala.com/posts/aiagent-ready-blockspace-by-phala-network)
Data & Trustworthiness
These projects are focused on providing high-quality, verifiable data and computation necessary for reliable, non-hallucinating agents.
**OriginTrail (The Knowledge Graph):** OriginTrail is critical for ensuring AI agents can reason with trusted, verifiable data. It powers the Decentralized Knowledge Graph (DKG), a network that anchors real-world facts and enterprise data into AI systems. This prevents agents from making decisions based on hallucinations, supporting applications from supply-chain traceability to DeFi risk modeling.
SingularityNET (The AI Service Marketplace): As a key part of the ASI Alliance, SingularityNET’s core focus is a decentralized marketplace for AI services. Developers can deploy AI models as services that agents can access and pay for using the native token, creating a global, open-source platform for AI development and deployment.
Crust Network (Decentralized Storage): While not purely an agent platform, Crust provides essential decentralized cloud storage. Agents often need to store the data they process and learn from. Crust ensures this data is stored privately, securely, and in a decentralized manner, supporting protocols like IPFS.
Giza Protocol (The Translator): Agents are good at code, but bad at DeFi nuances. Giza uses the Model Context Protocol (MCP) to “translate” complex financial concepts into something an AI can safely reason about, allowing agents to manage portfolios without accidentally draining funds.
Nature’s Lesson: Stigmergy
How do these tools work together without a manager shouting orders? They use Stigmergy—a fancy word for “leaving a sign for the next guy”.
Nature: An ant finds food and leaves a chemical trail (pheromone) on the ground. The next ant smells it and follows.
Crypto: Blockchain is the digital ground. An AI agent doesn’t need to DM every other agent to say, “I finished the job.” It simply records a transaction on the ledger.
The rest of the swarm sees this immutable “digital footprint” and reacts immediately. This allows thousands of agents to sync up without ever speaking directly.
The Real Problems with Agent Swarm
However, we are moving from AI that just talks (like ChatGPT) to AI that actually does things. Giving software the freedom to act on its own can lead to messy problems. Before we can let swarms of autonomous agents run critical infrastructure, we have to fix three major issues identified by researchers at IBM and MIT.
The “Black Box” Problem (Trust)
The scary thing about modern AI is that it doesn’t follow a strict rulebook like old software. It makes guesses based on probability.
We don’t know “Why”: If an agent denies a loan or crashes a drone, we often can’t look inside to see exactly why it made that choice.
They move too fast: Agents can make thousands of decisions in the time it takes a human to blink. There is no way for a human manager to approve every single action, which means we are often flying blind.
The “One Brain” Weakness (Security)
Right now, most AI agents are controlled by a central server. In security terms, this is a nightmare.
Single Point of Failure: If you hack the central server (the “brain”), you control the entire fleet of agents.
Easy to Trick: If an attacker feeds bad data to that central brain, every agent connected to it starts making mistakes. It’s like putting all your eggs in one very fragile basket.
The “Liar” in the Group (Coordination)
This is the specific problem that stops robot swarms from working in the real world (often called the “Byzantine Generals Problem”).
Who do you trust? Imagine a swarm of drones delivering packages. If one drone gets hacked and starts sending fake GPS data to the others, how does the group know it’s lying?
The Ripple Effect: Without a way to verify the truth, one “bad apple” can confuse the whole swarm, causing them to crash or fail the mission. Current systems don’t have a good way for robots to vote on what is true without checking with a central boss.
Part 3: The Infrastructure – Ethereum’s New “Agent Standards”
For this agent society to function at scale, the underlying blockchain needed to evolve, here, we mainly talk about innovations in the Ethereum ecosystem, as Ethereum is a leading smart contract chain in the space right now. A swarm of 10,000 agents cannot operate if every transaction costs $5 or requires a credit card. Three recent innovations have specifically targeted these bottlenecks.
1. The Wallet Problem: x402 and the Machine Handshake
x402 protocol and How it empowers the Agentic Economy
In the traditional web, payments are designed for humans: credit card forms, CAPTCHAs, and billing addresses. An AI agent cannot navigate these.
The x402 Protocol solves this by reviving the dormant HTTP 402 “Payment Required” status code. Elastic Hub did publish an article talking about x402, which can be read here.
The Mechanism: When an agent requests a premium resource (e.g., a high-end GPU cluster), the server denies the request with a
402error and attaches a crypto invoice.The Resolution: The agent automatically signs a micro-transaction (e.g., 0.01 USDC on Base or Solana) and resends the request with the proof of payment in the header.
The Impact: This enables “Streaming Payments” for APIs. Agents don’t need subscriptions; they pay strictly for what they use, millisecond by millisecond, allowing for a fluid, permissionless economy.
2. The Cost Problem: ERC-8003 (Sentinel Storage)
Economic viability is the biggest threat to agent swarms. On Ethereum, initializing a storage slot (like setting a new account balance from 0 to 1) is one of the most expensive operations (20k gas). If a swarm spawns 1,000 temporary agents, the “setup costs” alone could bankrupt the operation.
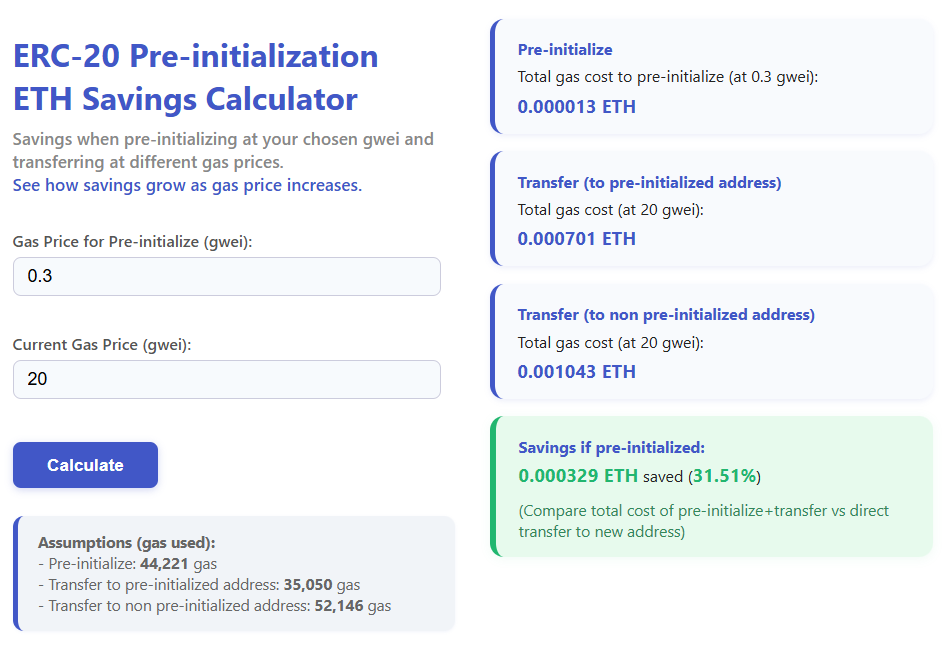
ERC-8003 introduces Sentinel Storage. It allows a master contract to “pre-initialize” storage slots during periods of low network congestion (low gas prices). Effectively, the swarm “buys” the storage capacity in bulk when it’s cheap. When the agents actually activate and start working, they write to these pre-paid slots at a fraction of the cost. This is the difference between buying retail and buying wholesale for computational resources.
3. The Identity Problem: ERC-8004 (Trustless Agents)
If an agent scams you and then deletes its code, how do you hold it accountable? ERC-8004 decouples the agent’s code from its reputation by minting the agent’s identity as a Non-Fungible Token (NFT).
Reputation Registry: Successes and failures are recorded against the NFT, not the ephemeral server instance. If an agent wants to be hired for a high-value task, it must present its NFT passport showing a history of successful jobs.
Portability: This identity is portable. An agent can move from AWS to a decentralized cloud like Akash, carrying its reputation (and its wallet) with it, ensuring that “Code is Law” applies to the entity, not just the server.
Part 4: The Safety Layer – Protecting the “Ghost in the Machine”
The challenge of securing an Autonomous Economic Agent (AEA) is fundamentally the “Confidential Computing” problem: how to process sensitive data (like an agent’s private keys or its proprietary trading strategy) in a cloud or network environment where the hardware owner (the node operator) is untrusted.
The solution, pioneered in the decentralized space by projects like Phala Network, is the use of Trusted Execution Environments (TEEs). These are not unique to Web3; they represent a major area of focus for hardware manufacturers and cloud providers aiming to protect data in use.
TEEs: The Core Security Mechanism
A TEE is a hardware-level secure enclave within a CPU or GPU. It creates a small, highly isolated environment that is entirely separate from the main operating system (OS), the hypervisor, and any other software running on the host machine.
Expanding the Landscape: TEE Providers & Protocols
The underlying hardware and general confidential computing solutions come from major technology providers and other decentralized protocols.
Hardware-Based TEE Vendors (The Foundation)
TEEs rely on specific features built into modern processors. These vendors are the foundation of all confidential computing solutions:
Intel SGX (Software Guard Extensions) / Intel TDX (Trust Domain Extensions): Intel’s technologies are widely used to create secure enclaves (SGX) and more robust Trust Domains for virtual machines (TDX). They are the most common TEEs deployed in cloud and Web3 confidential computing.
AMD SEV (Secure Encrypted Virtualization): AMD’s technology focuses on encrypting the entire virtual machine memory, protecting it from the hypervisor. This is often used for broader workload confidentiality rather than small, granular enclaves.
NVIDIA TEE: More recently, high-performance GPUs (like the H100) are including TEE capabilities to protect large AI model weights and inference data during execution, which is vital for running large language models (LLMs) securely within decentralized agent networks.
Decentralized TEE Protocols
These projects leverage the hardware TEEs to build a decentralized, censorship-resistant network for agents.
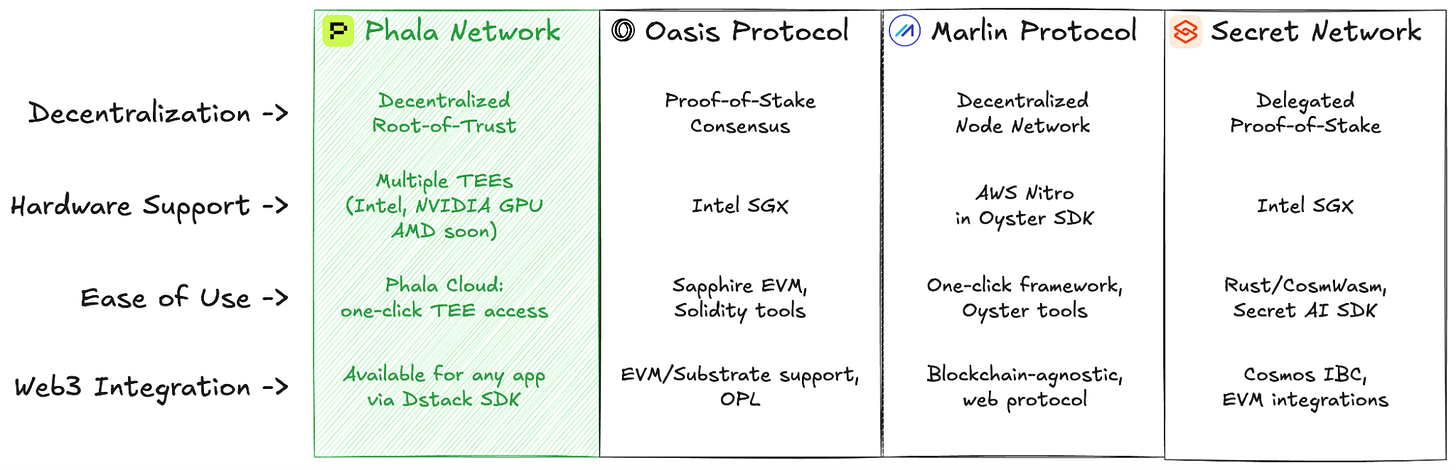
Phala Network: As you mentioned, Phala abstracts the TEE hardware into a decentralized confidential computing cloud. It allows developers to deploy standard applications (including AI models) into TEEs without needing to be the cloud provider themselves, making agent execution verifiable and private.
Secret Network (for Confidential Smart Contracts): Secret Network pioneered the use of TEEs to create “secret contracts,” which allow smart contract inputs, outputs, and state to remain encrypted. This is key for agents that need to manage private inputs (like market orders or sensitive data) while running on a public blockchain.
Oasis Network: Oasis uses TEEs (specifically Intel SGX) to power its ParaTimes (separate execution environments) for privacy-preserving computation, enabling agents to process sensitive data with both confidentiality and scalability.
By combining the decentralization of the network layer (Fetch.ai, ASI) with the hardware-enforced security of TEEs (Phala, Secret, IBM), the “Ghost in the Machine” is finally protected, allowing true, auditable, and secure Autonomy.
The result is a shift from Automation (scripts that do what they are told) to Autonomy (agents that decide how to achieve a goal best). By moving the logic from centralized servers to decentralized, verifiable ledgers, we are building antifragile systems—swarms that don’t just survive volatility, but use it to negotiate, adapt, and optimize the world’s digital work.