Privacy is the default future of Crypto
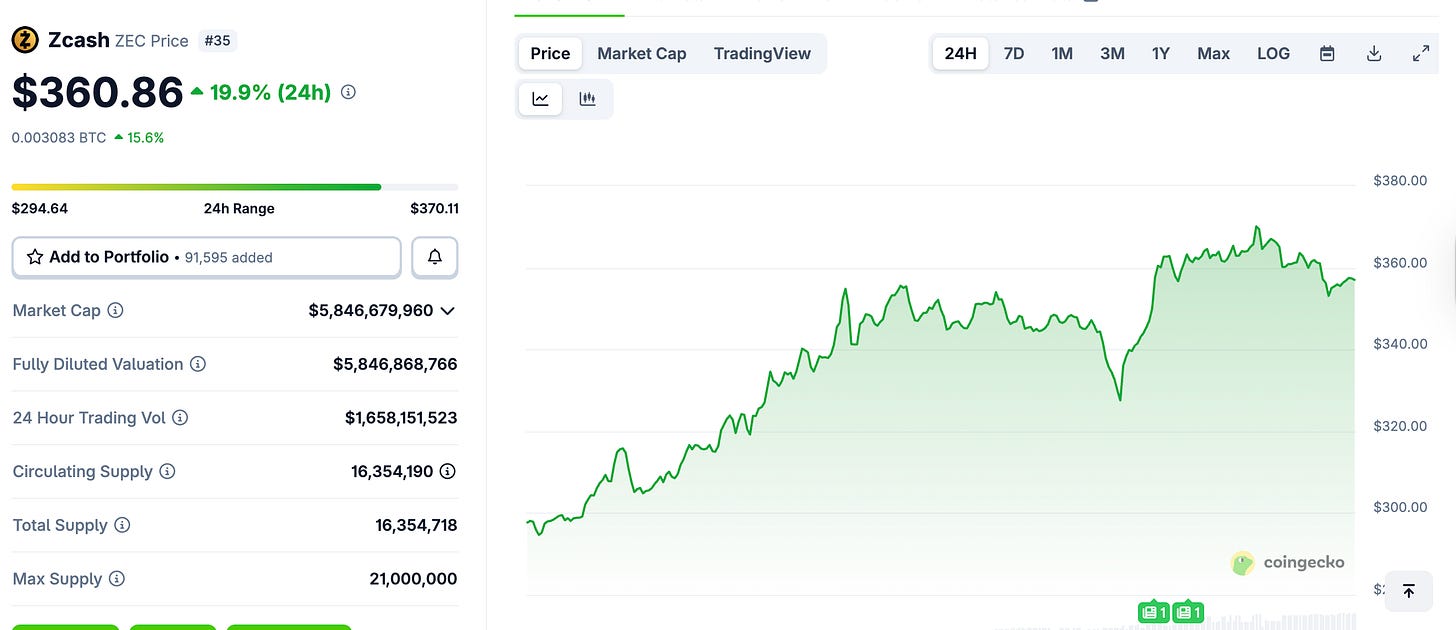
Zcash’s recent comeback in valuation has reignited a long-overdue discussion: should privacy be a default feature of every decentralized application?
To dive deeper, let’s begin with a simple scenario:
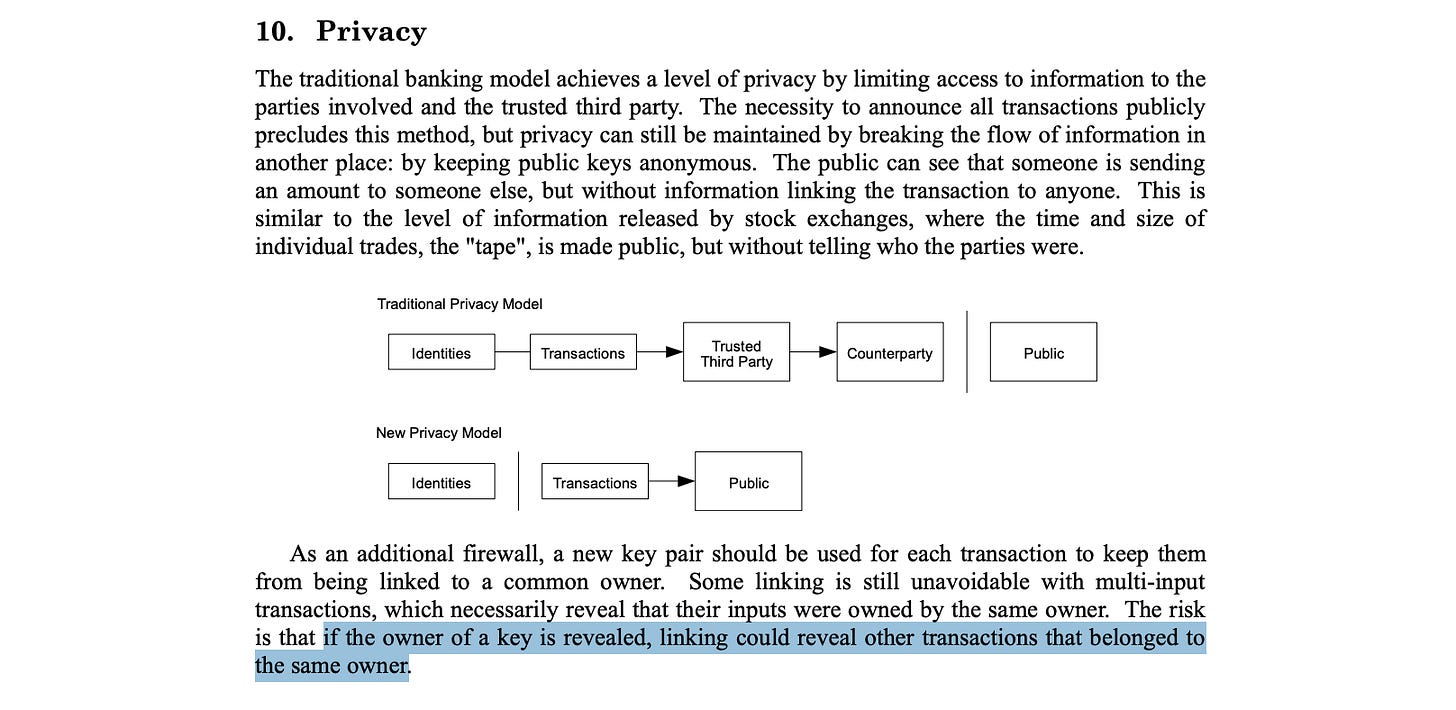
A shop accepts crypto payments. When a customer pays, the cashier can instantly look up that wallet’s past activity, where it’s been used, how much it holds, and even the pattern of spending.
That’s like making your entire credit card history public for anyone to see.
This is the world of transparent blockchains today. Every transaction is visible. While transparency helps build trust in decentralized systems, it also opens the door to data abuse, tracking, and profiling, risks that limit everyday use.
Actually, most of us have seen this story before. In the early days of the internet, websites used a protocol called HTTP (Hypertext Transfer Protocol). It was fast, but not private; anyone could intercept your personal data. The problem was solved by HTTPS (Hypertext Transfer Protocol Secure), which added encryption and made online banking and e-commerce possible in today‘s internet.
And the next wave of blockchain innovation promised to do for finance what the internet did for information, making it faster and borderless, but its radical transparency turned out to be a double-edged sword. People often assume that because blockchains use wallet addresses instead of names, they are anonymous. But in truth, they are pseudonymous.
As the Bitcoin White Paper warned:
Once a user’s wallet address is linked to a real-world identity, that person’s entire financial history becomes public for anyone. What was meant to represent decentralization and freedom instead exposes users to the kind of visibility no one would accept in normal life.
Without balanced privacy, the blockchain economy cannot evolve to become a system people trust for real-world use. Everyday users need to feel safe, like online banking or e-commerce provides today. They must know that their activities are protected, that transactions are private by design.
In the same way that encryption trans formed the early internet from a fragile experiment into a trusted global infrastructure, on-chain privacy represents the next layer that will make decentralized systems truly usable at scale.
Types of Privacy-Enhancing Technologies (PETS)
When we talk about privacy on the blockchain, there isn’t just one way to achieve it. Different technologies are being explored, from mixnets and confidential transactions to privacy layers built directly into smart contract protocols.
Zero Knowledge Proof
ZK-proof is a cryptographic method that allows one party, called the prover, to convince another party, the verifier, that something is true without revealing any of the information that proves it. In other words, it allows users to prove they know something without revealing the data itself.
A simple way to think about this is how websites check your password. When you log in, you don’t actually send your real password every time; instead, your password is turned into a cryptographic hash, and the website only checks whether that hash matches what it already knows. You’ve proved you know the password — without ever revealing the password itself.
ZK Proof works in a similar way but with much greater complexity: you can prove a statement is valid without revealing any of the private information behind it.
On blockchain, this means users can verify transactions, ownership, or eligibility without exposing their full wallet balances, history, or identity. Instead of revealing everything, they share a succinct proof that confirms the transaction’s validity.
This approach unlocks two major advantages: privacy and scalability.
Confidential Transactions:
ZK-proofs can hide transaction details such as the sender, receiver, or amount being transferred, while still proving that the transaction follows all network rules. This is the foundation of privacy-focused projects like Zcash, which pioneered shielded transactions, and newer designs like privacy pools, which allow users to prove their funds are not linked to illicit sources without revealing their entire transaction graph.
Aside, Zcash is becoming very famous as a privacy token due to the vision as a pure privacy token at the top of mind and simple privacy functionality of the network itself, even Sergey Brin (Google Founder) mentioned Zcash when talking about privacy.
Efficient Scaling:
ZK-proofs also make blockchains more efficient. Instead of requiring every node to re-check every transaction, validators can verify a small proof that batches thousands of them at once. This technique is what enables high-performance projects like zkSync, StarkNet, and Succinct to deliver faster, cheaper, and more scalable blockchain environments — all while maintaining full security.
There are two main types of ZK systems: SNARKs (Succinct Non-Interactive Arguments of Knowledge) and STARKs (Scalable Transparent Arguments of Knowledge). SNARKs are compact and efficient but rely on a trusted setup, while STARKs remove this dependency, offering greater transparency, stronger cryptographic assumptions, and even protection against future quantum attacks.
Although generating these proofs still requires heavy computation, continuous progress in acceleration is rapidly reducing costs and latency, making ZK-proofs increasingly practical for real-world use.
Recent Succinct launch’s SP1 zkVM and decentralized prover network make zero-knowledge proofs more widely used and popular by enabling efficient and scalable generation of proofs and providing an on-demand marketplace that lowers barriers for developers across various applications.

Fully-Homomorphic Encryption (FHE)
The core idea behind FHE is simply about performing calculations on encrypted data without ever decrypting it.
In normal encryption, data must first be decrypted before any operation can take place. Imagine sending an encrypted note to a service and asking it to add two numbers written inside. To do that today, the service would need to decrypt your note, read the numbers, perform the addition, and then re-encrypt the result, which exposes your private information in the process.
With Fully Homomorphic Encryption, the same calculation can be performed while the note stays encrypted. The system manipulates the encrypted data itself, never seeing the underlying numbers, yet the result is exactly the same as if it had been done on the original plaintext.
This unlocks entirely new possibilities for how privacy can exist in blockchain and cloud environments:
Confidential Smart Contracts:
FHE could enable a new generation of on-chain applications where data never leaves its encrypted state, even while it’s being processed. Developers could build private decentralized exchanges, lending protocols, or tokenized asset systems where user balances, bids, and collateral values remain hidden but still fully verifiable.
Secure Data Processing:
Users can send sensitive information — such as financial records, medical data, or machine-learning inputs — to be processed on-chain or off-chain, without validators, service providers, or algorithms ever seeing the raw data. This approach could protect user privacy while still enabling valuable analytics or AI-driven insights to occur.
The latest partnership between Zama and OpenZeppelin offers an open-source Confidential Contracts Library on GitHub, providing primitives for secure, encrypted computations on EVM-compatible blockchains via Zama’s fhEVM coprocessor.

Trusted Execution Environments (TEEs)
While most blockchain privacy tools rely on cryptography, Trusted Execution Environments (TEEs) provide privacy at the hardware level. A TEE is a secure enclave within a processor that runs code and processes data in isolation, keeping it hidden even if the operating system or surrounding software is compromised. In essence, it creates a small vault inside the chip where sensitive data can be safely used without ever being exposed.
A good example is in cloud computing, where TEEs allow encrypted data to be analyzed without revealing it to the service provider. The information is processed inside the enclave, then re-encrypted before leaving, meaning the system completes the computation without ever seeing the raw content.
In short, TEEs are highly efficient. Their main computational cost is small and only occurs when entering or leaving the secure hardware area and encrypting/decrypting data.
Multi-Party Computation (MPC)
Multi-Party Computation takes a different approach to privacy by enabling several participants to jointly compute a result without revealing their private inputs to one another, creating a form of shared computation where everyone contributes, but no one exposes their data.
Imagine a group of people who want to calculate the average of their salaries without anyone disclosing their actual income, each input staying private while the correct output is still computed collectively. This principle now underpins many blockchain applications, especially key management systems like Fireblocks, Privy, where private keys are split into cryptographic shares distributed across multiple devices or servers so that no single party ever holds the full key, yet all can still sign transactions together securely.
Ring Signatures
With Ring Signatures, when a user wants to authorize a transaction, their digital signature is combined with those of several other participants to form a group. To anyone observing the blockchain, the transaction appears to have been signed by someone in that group, but it’s mathematically impossible to determine who the real signer was.
The most recognized project in crypto community is Monero, one of the earliest and most consistent projects to prioritize privacy as a default. Every transaction in Monero uses ring signatures to obscure the sender’s identity, making it extremely difficult to trace the source of funds back to a single person. This level of anonymity has made Monero a point of debate in the larger conversation about privacy and regulation.
The debate on privacy solutions
There is an ongoing debate on “who wins privacy” in crypto, which centers on balancing privacy, verifiability, and interoperability, while ensuring regulatory compliance and user-friendly performance. The general consensus is that no single solution dominates; the best approach depends on use cases like transactional privacy, encrypted computations, or enterprise needs.
Privacy Coins ( Zcash): Simple, sovereign privacy for transactions, but isolated and regulation-constrained.
ZK Infrastructure (ZKSync’s Prividium, Starknet): Scalable, compliant proofs with Ethereum compatibility; strong for enterprises but faces UX challenges.
Encrypted Computation (Arcium): Enables private data processing (e.g., AI); powerful but computationally heavy and early-stage.
Enterprise Models (Canton): Private, consortium-based DLTs for businesses; limited by silos and lack of public verifiability.
Hybrids (Fairblock): Combine ZK, FHE, and MPC for programmable privacy across use cases; favored for flexibility but complex.
Check the debates:
https://x.com/0xMert_/status/1980034554434900145
https://x.com/kayprasla/status/1980036861226889433
https://x.com/JasonYanowitz/status/1980016838269366504
https://x.com/s33dkn33/status/1980267170400530591
Opportunities For Application Builders
The shift is already happening: privacy is moving from a backend feature to a front-end experience that shapes how users trade, pay, build, and interact on-chain.
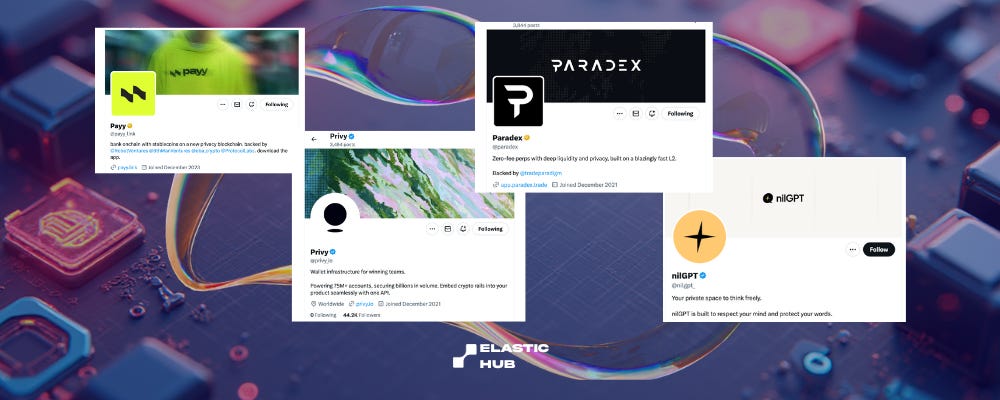
Across the ecosystem, several projects are leading this wave:
Payy: Private payment rails for seamless, confidential crypto transactions.
Paradex: Decentralized perpetuals exchange focused on trader privacy and compliance.
Privy: Privacy-first identity and wallet infrastructure for onboarding and data control.
nilGPT: Privacy-preserving AI chatbot using Nillion’s blind computation for secure encrypted inference.
And many more, privacy would be a default optional feature for users in every consumer application. For developers, this new landscape represents more than just protecting user data; it’s about building trust into every layer of the product stack.
Closing Thoughts
Not just a major innovation in privacy infrastructure, the real shift today is about how privacy can coexist with regulation without sacrificing the open, verifiable nature of blockchain. As networks evolve, privacy is no longer a niche feature. The goal isn’t to hide, it’s to protect users while proving the truth. I’ll explore how these principles unfold in real-life case studies in an upcoming article.
Written by @crisnguyen99 (Twitter)